GitOps with Meshery
 MeshMap Snapshot GitHub Action
MeshMap Snapshot GitHub Action
- See your deployment before you merge
- Connect MeshMap to your GitHub repo and see changes pull request-to-pull request
- Get snapshots of your infrastructure directly in your PRs
Using Meshery's SnapShot GitHub Action
See your deployment before you merge. Connect MeshMap to your GitHub repo and see changes pull request-to-pull request. Get snapshots of your infrastructure directly in your PRs.
See Extension: MeshMap Snapshot for more details.
 Service Mesh Performance GitHub Action
Service Mesh Performance GitHub Action
- See your performance regressions before you merge
- Connect Performance Management to your GitHub repo and see changes pull request-to-pull request
- Red light performance regressions
- Baseline and analyze the performance of your services is key to efficient operation of any application
- Meshery is the canonical implementation of the Cloud Native Performance specification
- Define your performance profiles upfront. See statistcal analysis with microservice latency and throughput quartiles
- Meshery includes your choice of load generator, so that you can meausure your way
- Meshery packages all these features into an easy-to-use GitHub Action
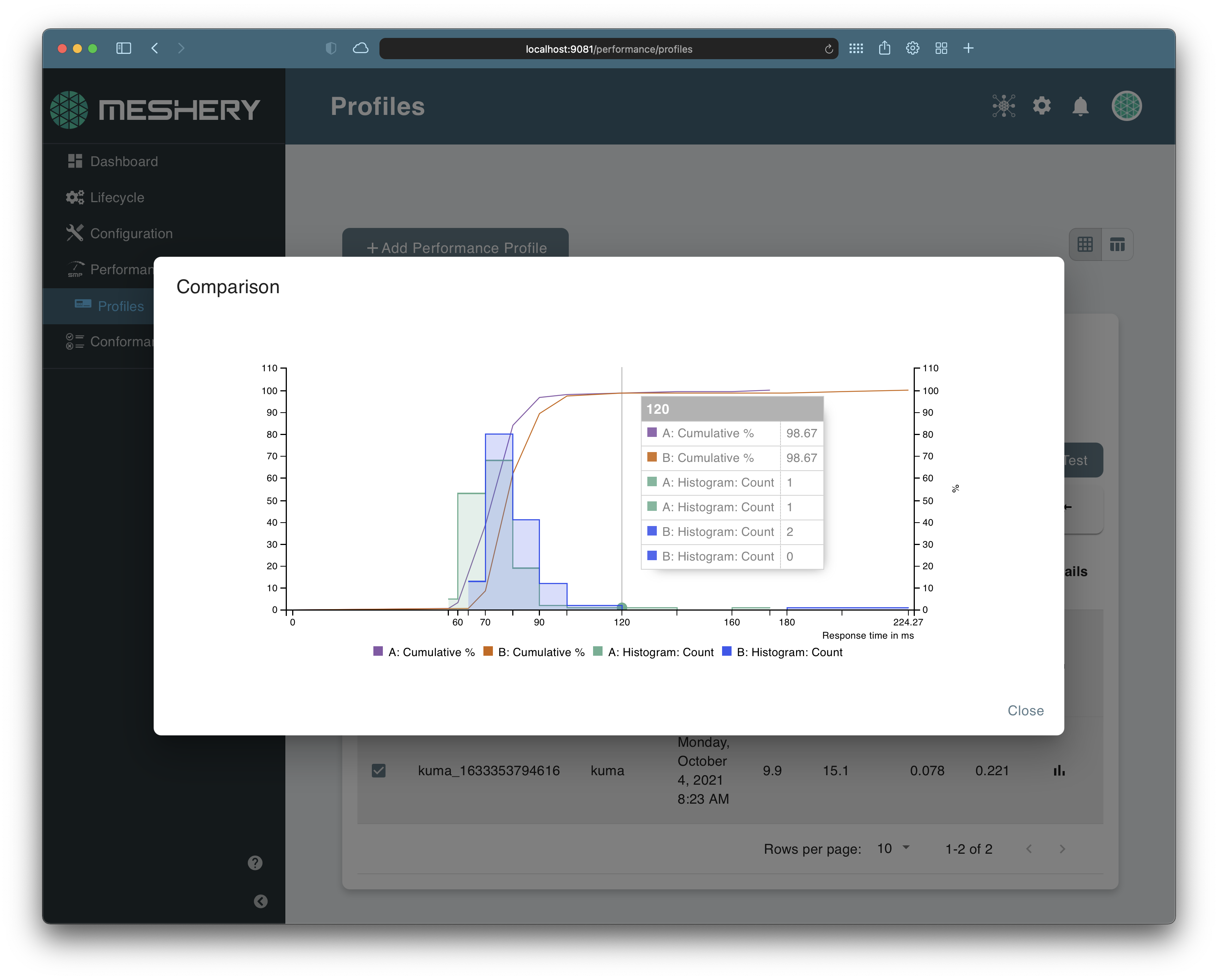
Measuring and managing the performance of a service mesh is key to efficient operation of any service mesh. Meshery is the canonical implementation of the Service Mesh Performance specification. You can choose from multiple load generators and use a highly configurable set of load profiles with variable tunable facets to run a performance test. Meshery packages all these features into an easy-to-use GitHub Action.
Using Meshery's Service Mesh Performance GitHub Action
The Service Mesh Performance GitHub Action is available in the GitHub Marketplace.You can create your own performance profiles to run repeatable tests with Meshery. You can configure this action to trigger with each of your releases, on every pull request. or any GitHub workflow trigger event. A sample configuration of the action is shown below.
name: Meshery SMP Action
on:
push:
branches:
'master'
jobs:
performance-test:
name: Performance Test
runs-on: ubuntu-latest
steps:
- name: checkout
uses: actions/checkout@v2
with:
ref: 'perf'
- name: Deploy k8s-minikube
uses: manusa/actions-setup-minikube@v2.4.1
with:
minikube version: 'v1.21.0'
kubernetes version: 'v1.20.7'
driver: docker
- name: Run Performance Test
uses: layer5io/meshery-smp-action@master
with:
provider_token: $
platform: docker
profile_name: soak-test
You can also define your test configuration in an SMP compatible configuration file as shown below.
smp_version: v0.0.1
id:
name: Istio Performance Test
labels: {}
clients:
- internal: false
load_generator: fortio
protocol: 1
connections: 2
rps: 10
headers: {}
cookies: {}
body: ""
content_type: ""
endpoint_urls:
- http://localhost:2323/productpage
duration: "30m"
See this sample GitHub workflow (action.yml) for more configuration details.
The results from the tests are updated on the Performance Management dashboard in Meshery. To learn more about interpreting the test results, check out this guide. You can always checkout the Meshery User Guides to dive deep into these features.
Service Mesh Performance standardizes service mesh value measurement, characterizing any deployment’s performance by capturing the details of infrastructure capacity, service mesh configuration and workload metadata.
Service Mesh Conformance GitHub Action (Archived)
Service Mesh Interface Conformance GitHub Action
 Service Mesh Interface provides a standard interface for service meshes on Kubernetes. These (currently) four specfications offer a common denominator set of interfaces to support most common service mesh use cases and the flexibility to evolve to support new service mesh capabilities over time.
The Meshery SMI Conformance Action which validates SMI conformance in your pipeline and the Meshery SMP Action which runs SMP compatible performance benchmarks.
Service Mesh Interface provides a standard interface for service meshes on Kubernetes. These (currently) four specfications offer a common denominator set of interfaces to support most common service mesh use cases and the flexibility to evolve to support new service mesh capabilities over time.
The Meshery SMI Conformance Action which validates SMI conformance in your pipeline and the Meshery SMP Action which runs SMP compatible performance benchmarks.
Service Mesh Interface Conformance GitHub Action
Conformance of SMI specifications is defined as a series of test assertions. These test assertions are categorised by SMI specification (of which, there are currently four specifications) and comprise the complete suite of SMI conformance tests. Conformance requirements will change appropriately as each new version of the SMI spec is released. Refer to Meshery's documentation for details of how Meshery performs SMI conformance.Using Meshery's SMI Conformance GitHub Action
The Service Mesh Interface Conformance GitHub Action is available in the GitHub Marketplace. You can configure this action to trigger with each of your releases, on every pull request. or any GitHub workflow trigger event. An example of the action configuration which runs on every release is shown below. The action handles setting up a Kubernetes environment, deploying the service mesh (see supported service meshes), running the conformance tests and reporting back the results to the SMI Conformance dashboard in Meshery.
name: SMI Conformance with Meshery
on:
push:
tags:
- 'v*'
jobs:
smi-conformance:
name: SMI Conformance
runs-on: ubuntu-latest
steps:
- name: SMI conformance tests
uses: layer5io/mesheryctl-smi-conformance-action@master
with:
provider_token: $
service_mesh: open_service_mesh
mesh_deployed: false
You can also bring in their own cluster with specific capabilities and with a service mesh already installed.
name: SMI Conformance with Meshery
on:
push:
branches:
- 'master'
jobs:
smi-conformance:
name: SMI Conformance tests on master
runs-on: ubuntu-latest
steps:
- name: Deploy k8s-minikube
uses: manusa/actions-setup-minikube@v2.4.1
with:
minikube version: 'v1.21.0'
kubernetes version: 'v1.20.7'
driver: docker
- name: Install OSM
run: |
curl -LO https://github.com/openservicemesh/osm/releases/download/v0.9.1/osm-v0.9.1-linux-amd64.tar.gz
tar -xzf osm-v0.9.1-linux-amd64.tar.gz
mkdir -p ~/osm/bin
mv ./linux-amd64/osm ~/osm/bin/osm-bin
PATH="$PATH:$HOME/osm/bin/"
osm-bin install --osm-namespace default
- name: SMI conformance tests
uses: layer5io/mesheryctl-smi-conformance-action@master
with:
provider_token: $
service_mesh: open_service_mesh
mesh_deployed: true
You can download a token from Meshery and add it as a GitHub secret (in the example above, the secret is MESHERY_PROVIDER_TOKEN). After the test is run, you can view the results from the Service Mesh Interface dashboard in Meshery UI.
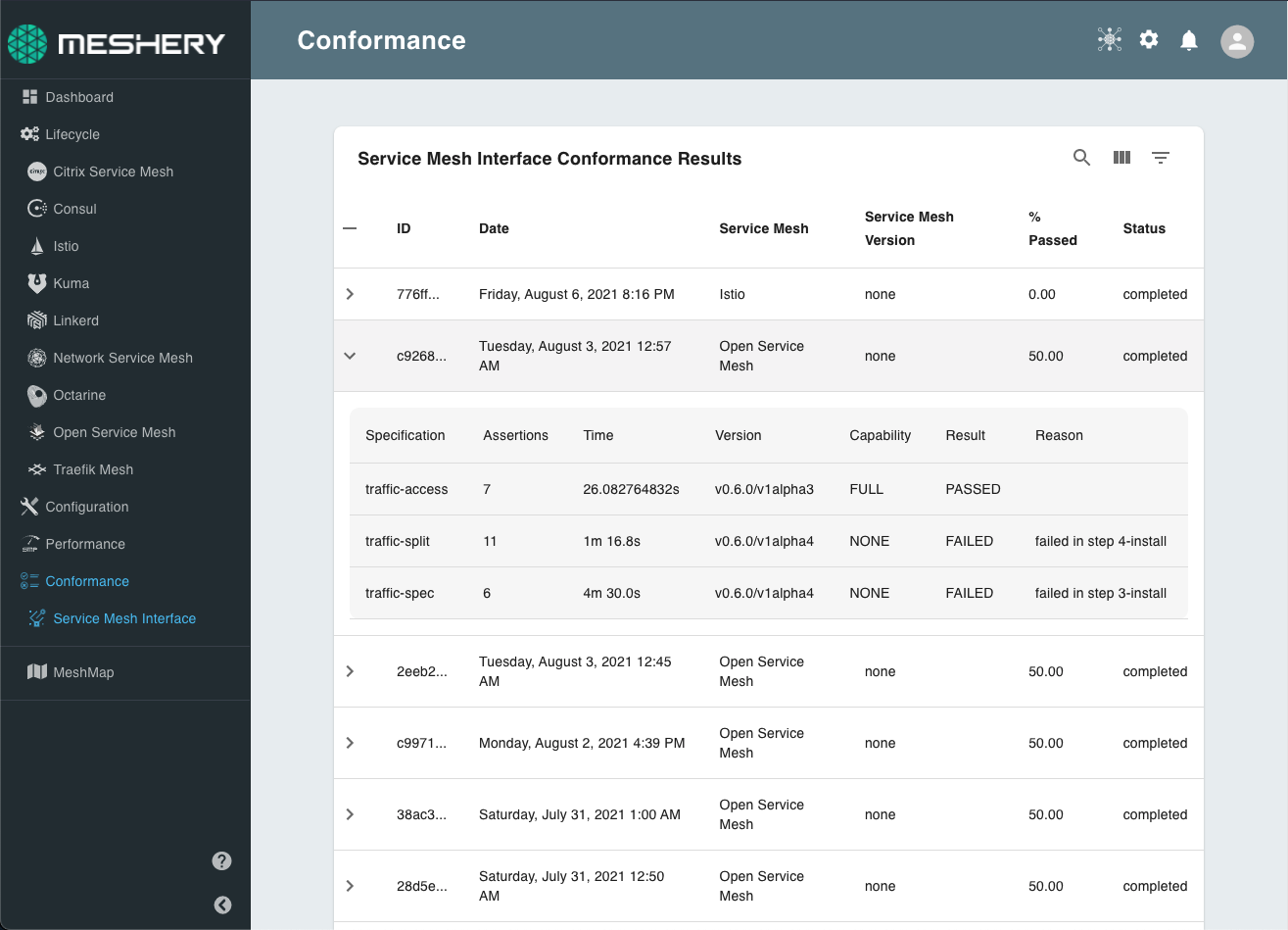
Meshery's Service Mesh Interface Conformance Results
Participating service mesh projects can also automatically report their conformance test results to the SMI Conformance dashboard